acl filter commands
Once the command has completed execution the filter becomes inactive. Syntax accelerate undo accelerate Default ACL acceleration is disabled.
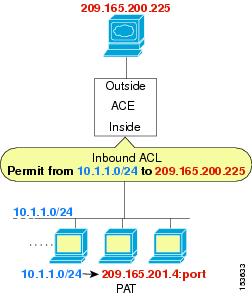
Cisco Content Hub Configuring Security Access Control Lists
Specify the ACL number here as the argument.
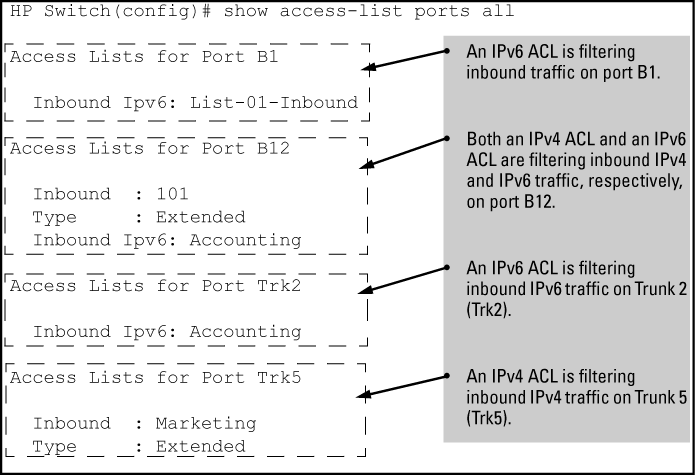
. Creating a standard ACL Access the CLI prompt of Router and run the following commands. ACL Commands Domain Name Server DNS Commands Energy Efficient Ethernet EEE Commands Internet Group Management Protocol IGMP Commands IP Commands Link Aggregation Commands Loopback Detection Commands Link Layer Discovery Protocol Commands Monitor Mirror Commands Port-Based Network Access Control Commands. When ACL is used as packet filter these ACEs are called packet filtering rules or conditions.
211 ACL Commands The list of CLI commands for the configuration of ACL is as follows. FirstAllows you to test the command against the first x records. The function limits the number of ACLrules.
For example select access-id if the DN is a user. An ACL is sequence of command s called the Access Control Entry ACE that are entered in specific sequence. Cl-acltool is a Cumulus Linux-specific userspace tool you use to administer filtering rules and configure default ACLs.
An ACL is the same as a Stateless Firewall which only restricts blocks or allows the packets that are flowing from source to destination. Using Default ACL. We use the second command to activate the ACLs on the interface.
BETWEEN NameDF all names starting with D E or F BETWEEN Amount26 amounts 2 and. ACL_- It is the ACL that we want to activate on the interface. Once applied ACL will filter every packet passing through the interface.
We can permit certain types of traffic while blocking others or we can block certain types of traffic while allowing others. Disable the deny-preemption function. Type - Enter the Type of DN.
The second command accepts one argument and one option. The full syntax of the standard ACL command is as follows. ACLs work on a set of rules that define how to forward or block a packet at the routers interface.
Observe the first command output in image there is extra sign after the permissions like -rw-rwxr this indicates there are extra ACL permissions set which you can check by getfacl command. Inout- It is the direction in which we want to activate the ACL. The specifics of sequence determine how ACL will behave so it recommended to include the most relevant ACE in the beginning of the ACL.
The access-list global configuration command defines a standard ACL with a number in the range of 1 to 99. DN Distinguished Name - Enter the DN Distinguished name of the entity requesting access to perform operations on the selected entry for example cnMarketing Group. Each ACL includes an action element permit or deny and a filter element based on criteria such as source address destination address protocol and protocol-specific parameters.
Select the False radio button to stop the accumulation of filter ACLs at the selected entry. If the ACLhas been sent to the hardware this command takes effect after resetting the firewall. The default ACL is a specific type of permission assigned to a directory that doesnt change the permissions of the directory itself but makes.
Note - The priority of ACL filters applied to the interface is based on the ACL numbers. Verify field Checks integrity of field with field type. Active500EMconfigno access-list deny-preemption 914 access-list ip extended.
Accelerate Use accelerate to enable ACL acceleration. If the ACL referenced by the traffic-filter or traffic-secure command is not referenced by other ACL-based. BETWEEN string min max Logical T or F Selects only records where the value is min and.
Routerenable Routerconfigure terminal Router configaccess-list 10 deny 10000 0255255255 Router configaccess-list 10 permit 20000 0255255255 Router config Lets discuss the above commands. By default the firewall must be enabled before using this command. If you want to filter.
Ip access-list mac access-list extended ipv6 access-list extended permit - standard mode deny - standard mode permit - IPv4 deny - IPv4. An ACL filter condition has two actions. Time to live ACL filter Range.
ECN ACL filter Range. Attaches bytes type. Access Control Lists ACLs are network traffic filters that can control incoming or outgoing traffic.
Use undo accelerate to disable ACL acceleration. Attaches shared policer to a rule. More tab Governs the number of records scope that will be processed.
VERIFY DATE T if record contain valid date. Reset acl counter reset packet-filter statistics rule IPv4 advanced ACL view rule IPv4 basic ACL view rule IPv6 advanced ACL view rule IPv6 basic ACL view rule Layer 2 ACL view rule user-defined ACL view rule comment step ACL commands acl Use acl to create an ACL and enter its view or enter the view of an existing ACL. Views IPv4 basicadvanced ACL view.
You can run the traffic-filter or traffic-secure command to configure packet filtering based on the following rules. DSCP ACL filter Range. Cl-acltool operates on various configuration files and uses iptables ip6tables and ebtables to install rules into the kernel.
Command filter A filter local to the command that is active only while the command is running. Commands and descriptions for distributed devices apply to the following routers. Both the traffic-filter and traffic-secure commands are used to filter packets and you do not need to configure both the commands on a switch.
The no form of the command unmaps ACL table with bind-point RIF from a VLAN interface. The priorityflag has no effect. The full syntax of the standard ACL command to filter a specific host is as follows.

Cisco Content Hub Configuring Security Access Control Lists
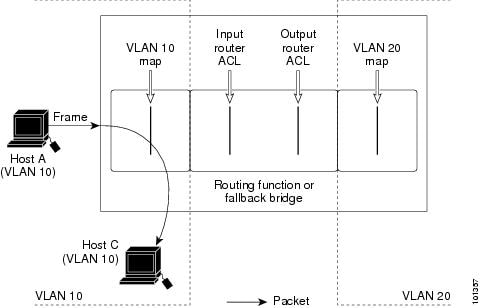
Security Configuring Ipv4 Acls Cisco Catalyst 3850 Series Switches Cisco Systems
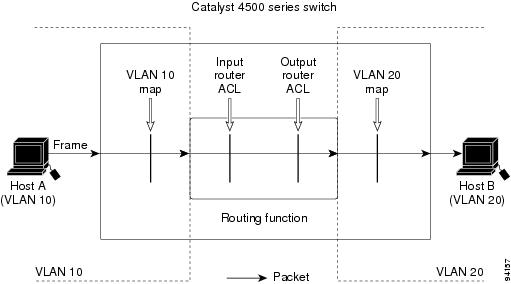
Catalyst 4500 Series Switch Sw Configuration Guide Release Ios Xe 3 2 Xsg Configuring Network Security With Acls Cisco Catalyst 4500 Series Switches Cisco

Cisco Access Control Lists Acl Cisconet Training Solutions

Configure Extended Ipv4 Acls Ccna 200 301
Access List Overview Chapter 6 Access List Introduction Part Iii Nonstateful Filtering Technologies Router Firewall Security Networking Etutorials Org

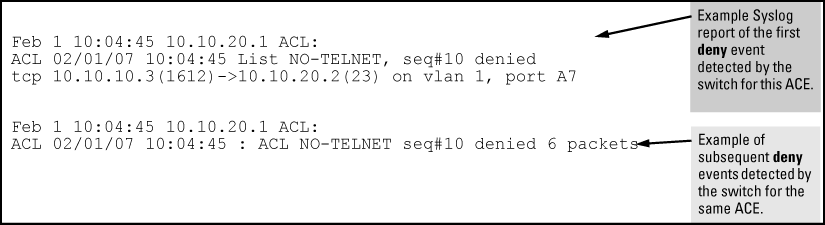



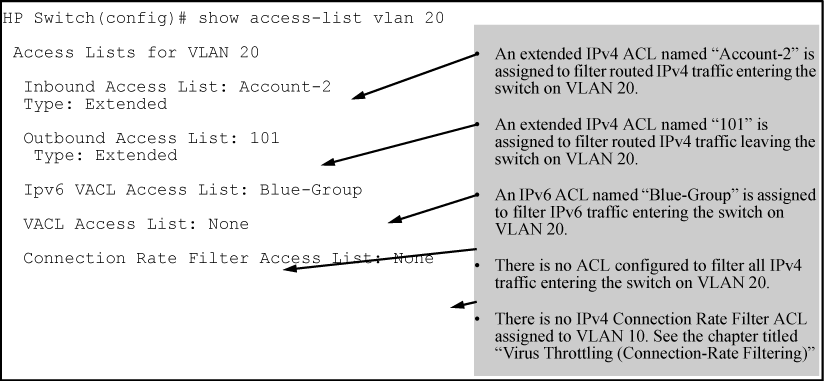
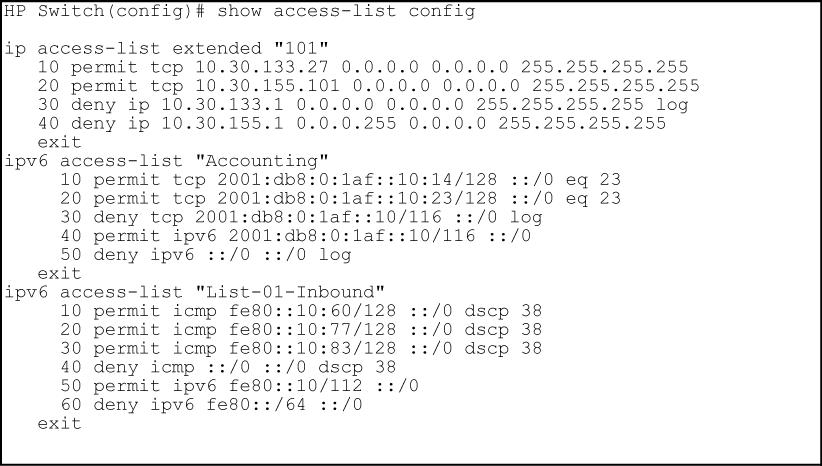


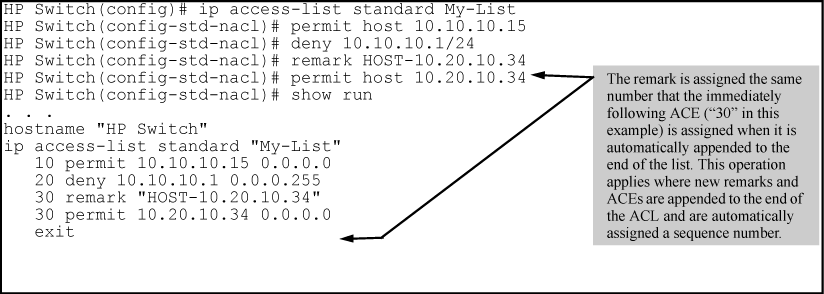

Comments
Post a Comment